Welcome to Open Vehicles
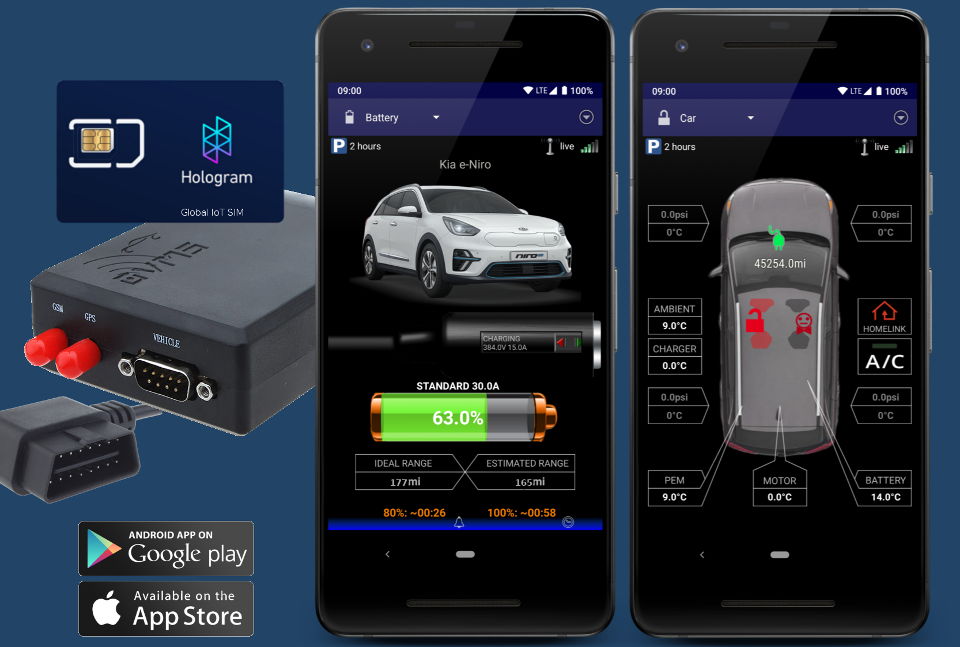
Open Source Electric Vehicle Telemetry
Monitor your Electric Vehicle from your Phone
Live Monitoring
We provide live monitoring of vehicle metrics like state of charge, temperatures, tyre pressures and diagnostic fault conditions. We work hard to provide as detailed information about the internals of a vehicle as possible.
Alerts
We will alert you, via PUSH notifications to your smartphone, to critical conditions and events like a charge abort, battery cell failure or potential theft.
Take Control
Depending on the vehicle integration we allow you to take control over the charge process, climate control, tuning parameters of the engine and more. Scripting capabilities, including interfacing to external charge control systems, take this to a new level.
Animate
Web and Phone
A built-in Web App user interface and remote control via native cellphone Apps available for Android and iOS. OVMS integrates into home/process automation systems via MQTT and provides data logging to SD card and to a server.
Open Source
OVMS enables you to add the features you want, working without regional restrictions, and giving you control over your personal data.
For Developers
Three CAN buses, a range of CAN tools, a configurable OBD2 translator, a DBC decoder, a reverse engineering toolkit and a CANopen client. The module provides SSH access and WebSocket streaming and can stream and inject CAN frames via TCP.


